Previously, when using a Cisco PIX firewall, VPN 3000 (Altiga), or other VPN hardware as an endpoint for a L2L or remote access VPN connection over the internet, 2 explicit internet facing interfaces were needed to allow internet access for these VPN connections. This was due to the fact that internet traffic would need to leave the internet interface (unencrypted)…..which is the same interface that the original encrypted traffic came in on. So it was simply not possible for this traffic to use a single interface to come in encrypted and leave unencrypted…a workaround to this if 2 interfaces were not available was to use split tunneling.
What is split tunneling? It uses ACLs to specify what traffic should be tunneled and what traffic should not be sent through the VPN. So traffic destined for all of the subnets on the corporate LAN will be sent through the VPN tunnel, and all other traffic (internet traffic) will NOT be sent over the VPN. The problem with this configuration is security – a system is connected to both the ‘trusted’ corporate LAN and the untrusted internet. In a standard, all-traffic-tunneled VPN, all network traffic from the remote endpoint (or network) is tunneled back to the corporate LAN and further internet access is controlled.
This is no longer the case. To start, lets take a look at exactly what were talking about:
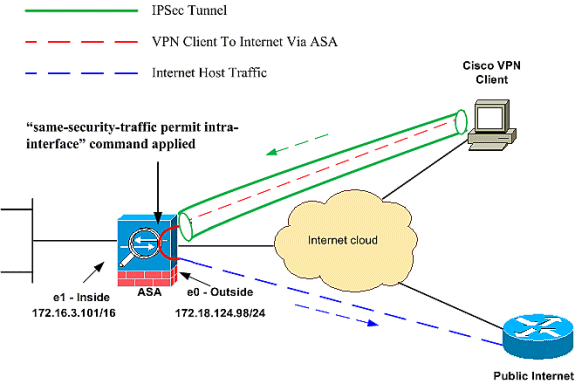
This is now possible using PIX or ASA code version 7.2 or higher and VPN client software version 5.x and later. Here’s the key commands to enable this configuration:
// Command that permits IPsec traffic to enter and exit the same interface. same-security-traffic permit intra-interface // Forces VPN Clients over the tunnel for Internet access. split-tunnel-policy tunnelall // The NAT statement to define what to encrypt (the addresses from the vpn-pool). nat (outside) 1 192.168.10.0 255.255.255.0
Note that if you have a range of IPs to be assigned to the VPN clients instead of an entire subnet, you will need to add the all of them to the nat (outside) to allow them to access the internet.
A complete configuration example is available from Cisco.com here.
