If you know anything about GSLB, you likely know that it is nothing more than a DNS trick that allows you to programatically return an IP (or CNAME) for a name based on service health or proximity to a location. But you may not know that you can also use GSLB in conjunction with Link Load Balancing to ensure that internal resources are highly available.
What is Link Load Balancing (LLB)?
Link load balancing is exactly what it sounds like – you are load balancing your external internet gateways\ISPs to provide for higher availability and higher throughput. *Note: this is NOT SD-WAN! The benefits of LLB are only realized when there are multiple outbound connections from different clients. Imagine the scenario:
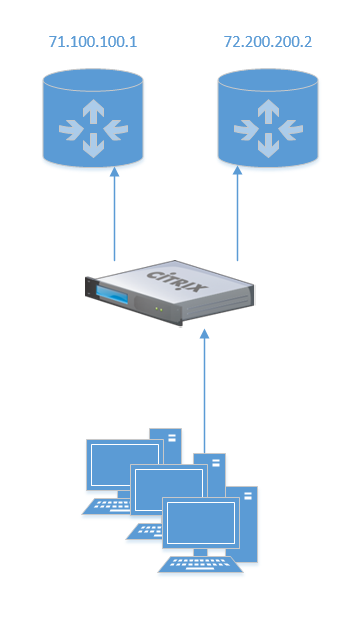
If you need to host some web service or application, you would traditionally just use a NAT and create a firewall rule – pretty simple. In this scenario, how would you make that highly available? There are a few ways to do this, and we’re going to use something I call Site Local GSLB on our Citrix ADC.
It should also be noted that you don’t need to be using LLB on the Citrix ADC – it can also be configured on your edge firewall\router as well. The only thing to remember for this GSLB configuration is that we need rules and translations for both sides.
Make Your NAT Highly Available
One method to making port forwards highly available would be to simply add both A-records with the different IP addresses such that multiple addresses are returned. But this doesn’t solve the problem when one of the links is down. This is where Citrix ADC comes in with GSLB – the most important point is that GSLB is just a glorified DNS trick, but normally it’s used between two sites. This is not to say that two sites are required, it is just the most common deployment.
To do this we will need many of the same things as in a traditional GSLB configuration:
- ADNS service on the ADC
- NAT for ADNS service (from both gateways)
- NAT for actual web service (from both gateways)
- GSLB sites (sort of)
- Delegated subdomain with NS records for both public IPs
- Lots of DNS records
ADC Configuration
This configuration assumes that you already have a basic understanding of GSLB and getting it configured on an ADC – if not a good place to start is here. We will also assume that you have already configured a ADNS service and GSLB site – note that we only need ONE site, and the public IP address will not be used since we will be using CNAME based GSLB services. The services will be active\passive in this example.
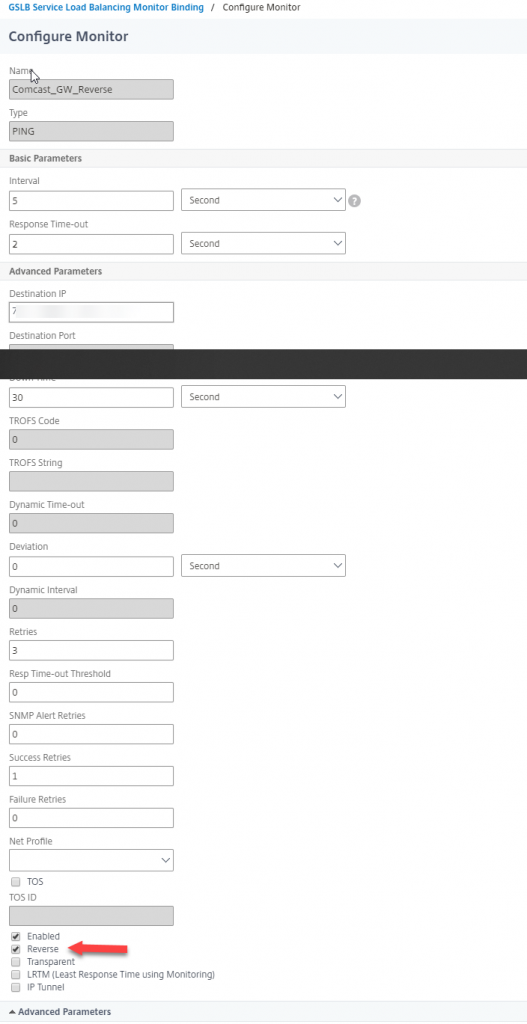
First, we need to create 3 monitors – one for each of the gateways in this example, then a third monitor for the backup gateway that is reversed. A simple ICMP monitor will work, with the destination being the next-hop of your ISP circuit. Here is a screenshot of the reversed monitor:
With the 3 monitors created, we will next create the GSLB services – one for each gateway, keeping in mind that naming needs to reflect the correct CNAME to be returned to the client that corresponds with the IP that is NAT’d via the primary gateway, and that we do NOT need to worry about IP addressing.
On the first service (the primary) add the monitor created for the primary gateway.
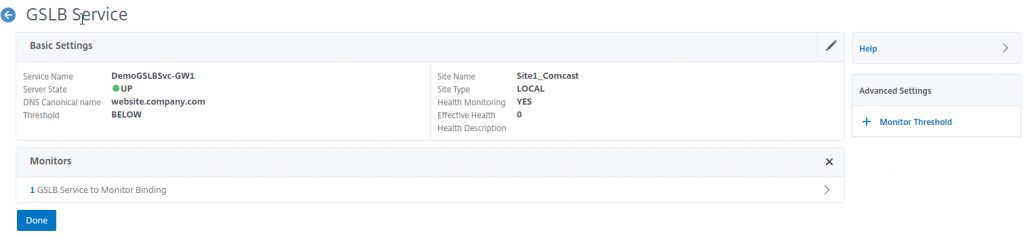
On the second GSLB service, we will add a monitor threshold of 10 and bind the secondary gateway monitor as well as the reverse primary monitor.
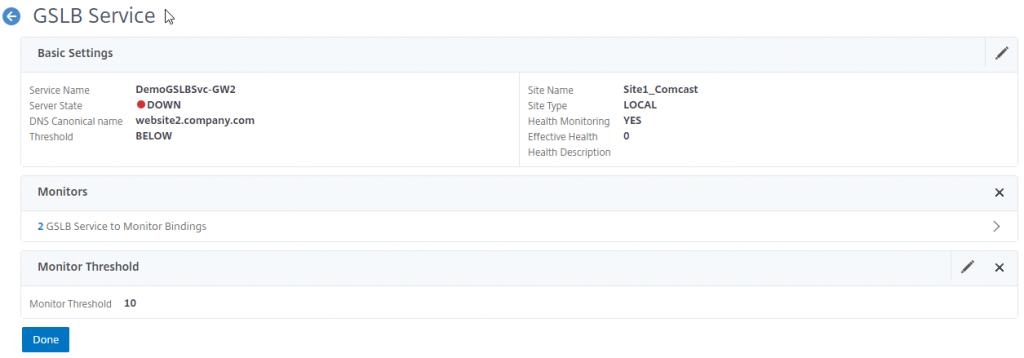
Bind the reverse monitor with a weight of 10.
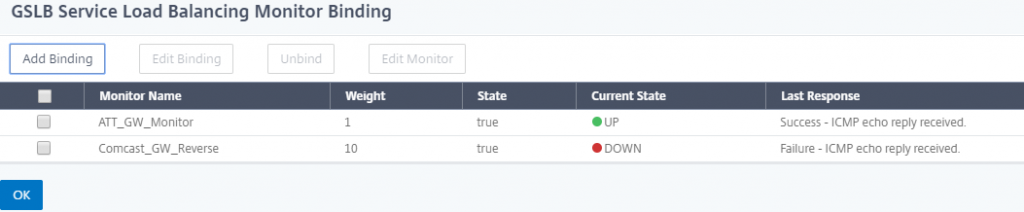
The reason we are using a reverse monitor and weighting here is due to the fact that most of the time, both gateways will be up, but we will only use 1. When the primary goes down, the primary monitor will go down, thus bringing the primary GSLB service down, but it will also flip the reverse monitor to up, thus bringing up the the secondary GSLB service.
Once the services are configured, and correctly showing as Up\Down, we need to create a GSLB vServer – note that we are creating a CNAME based GSLB vServer. Bind the previously created services, and set the FQDN for the GSLB domain.
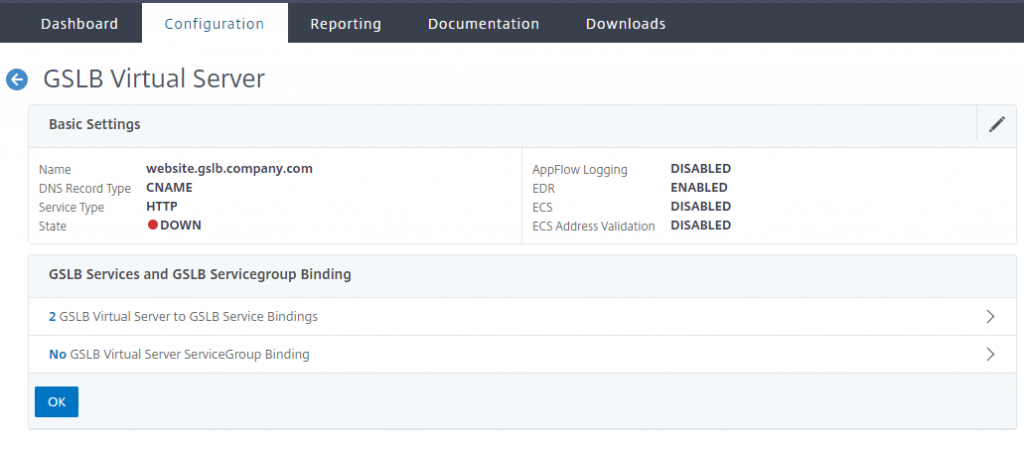
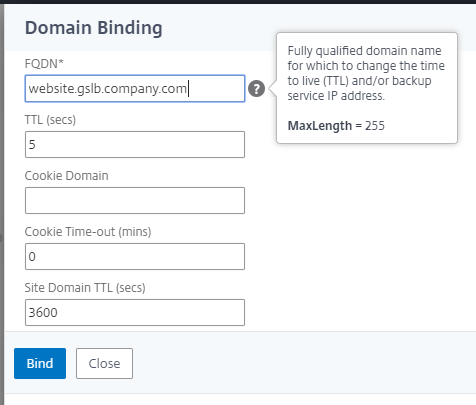
The ADNS service should automatically bind to your existing ADNS service – if not, you will need to create one and bind it.
Public DNS Changes
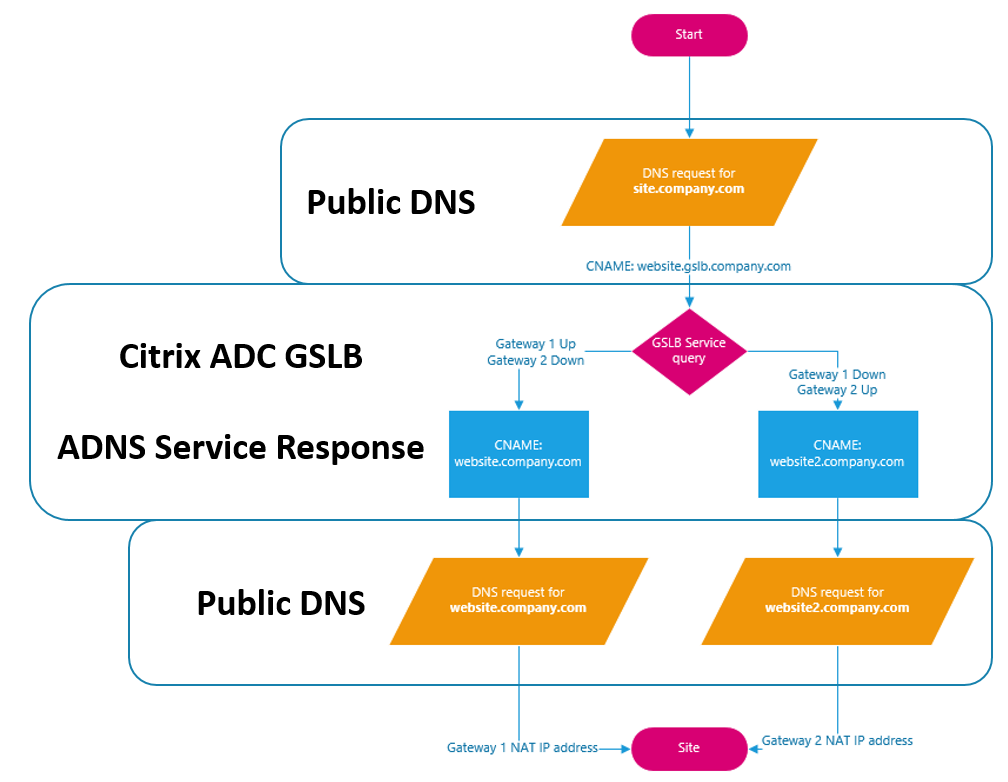
The last pieces of configuration needed are a few changes to DNS records – these changes should be the last changes made. Address records need to be created on PUBLIC DNS servers to match the CNAMEs that are returned, in this example, you would need to create an ARecord for website.company.com that points to 71.100.100.1 and an ARecord for website2.company.com that points to 72.200.200.2
A CNAME record needs to created on PUBLIC DNS servers for the original site that the user requests – for example, site.company.com will be a CNAME for website.gslb.company.com. Ensure that gslb.company.com is a delegated subdomain which points to the ADNS service on the ADC with SOA NS records for BOTH public IP addresses in this example (and the associated firewall rules to allow DNS traffic to the ADNS service through BOTH NATs).
Testing and Validation
Once all of the DNS changes have been made, the easiest way to test is to simply change the gateway monitor bindings (or even the monitors themselves) to bring down the primary GSLB service. Once that is done, you will get a different response from the ADNS service. The easiest way to test this is with nslookup or dig. The flow will look like the following: