Some background
There have been several questions and comments around the first post that describes a workaround to get Duo multi-factor authentication working with NetScaler (Citrix ADC) and nFactor. The issue stems from the fact that nFactor authentication uses both advanced authentication policies and it uses the RfWebUI theme – so if either of these conditions were met in your configuration, you were greeted with a rather ugly and non-functioning UI like this:
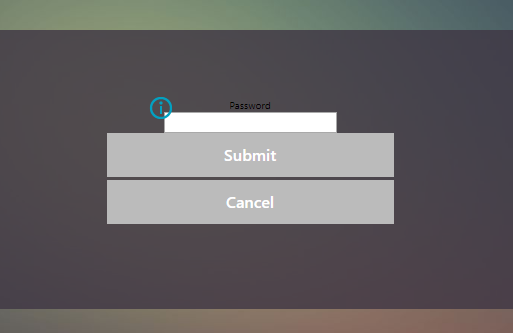
Good news, everyone!
Changes have been made both in the NetScaler code as well as the Duo authentication proxy code to allow for the native Duo Prompt iFrame to display correctly! So if you want to deploy Duo with advanced authentication policies on the NetScaler, this is the configuration for you. Fortunately, there’s not too much that is needed:
- NetScaler (Citrix ADC) needs to be running at least 12.1 build 50.x or later for the updated jquery that allows this to happen
- The Duo authentication proxy service needs to be running the 3.1 July 2019 build or later (though it is not noted in their release notes)
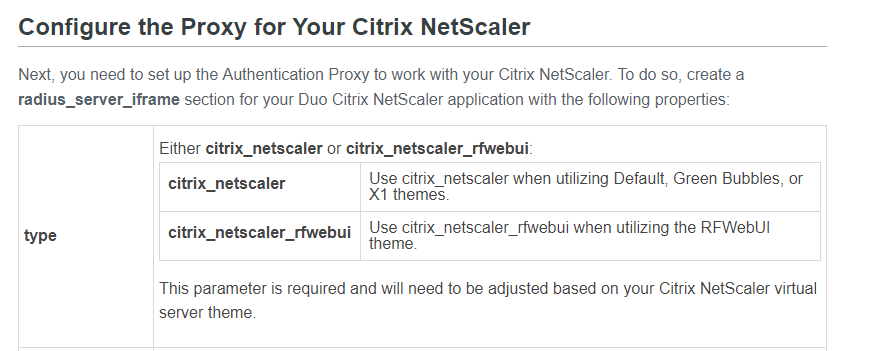
- The authentication proxy configuration needs to have the type set to citrix_netscaler_rfwebui rather than citrix_netscaler
- Changes to your nFactor authentication policies
And that’s it – you will now be able to render the full Duo Prompt iFrame in conjunction with nFactor authentication!
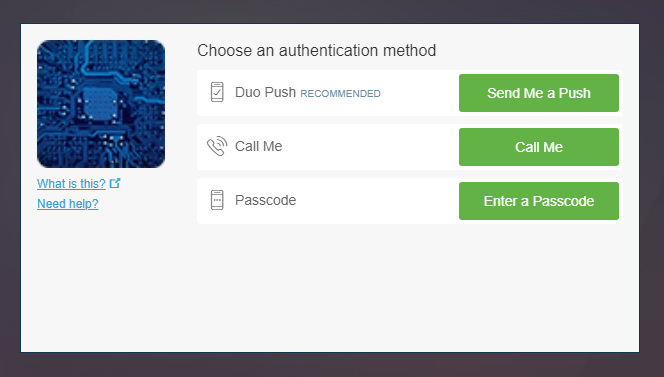
The nuts and bolts
There is not too much that is different with this scenario on the NetScaler, as you are now able to use the Duo Prompt either as a standalone authenticator (where the auth proxy is also doing AD\LDAP validation) configured only as a RADIUS server, or as a 2nd (or 3rd, or Nth) factor after letting the NetScaler do AD\LDAP, EPA and whatever other authentications.
The Duo authentication proxy configuration that needs to change is the type:
The full documentation is listed here: https://duo.com/docs/citrix-netscaler
If you’d like to see a full example configuration for the NetScaler, take a look over at Jason’s post here.
Why do I need this?
There are a few problems with the workaround posted initially – not rendering the full Duo Prompt prevented some significant things from happening:
- Users that had not yet enrolled any devices were not able to do so using the workaround…meaning that they would have to have the device setup outside of the logon page
- Users did not have the option to use SMS (which I guess is still a thing…I did not test this claim, but it was reported)
- Users that had multiple devices enrolled could not select which device they wanted to authenticate with
That being said, if the above scenarios don’t apply to you, the workaround implementation may be a better option as it is (in my opinion) a much cleaner and faster experience. The iFrame is rendered at your Duo API server, so there is a few seconds of delay while this is happening. The frame does get cached, so it does not happen every time, but could potentially lead to user confusion as nothing gets displayed in the delay time.

Hi Jake, i followed your article to setup Duo radio button earlier. Now i wanted to test iFrame and implement it for a uniform user experience. However, i am getting the following error on Auth proxy.
{“username”: “username”, “status”: “Error”, “client_ip”: null, “server_section”: “radius_server_iframe”, “timestamp”: “2019-09-25T06:56:44.597000Z”, “auth_stage”: “Primary authentication”, “factor”: null, “msg”: “No password provided”}
Hi Srinivasan, that log looks like the Duo auth proxy is configured to be the primary authentication, meaning that it is expecting a username and password that it will use to authenticate against AD. This is certainly an option along with pure RADIUS where DUO is configured with simply a username and does not do any authentication.
After i get this all setup and working, I get the DUP Prompt and it accepts it, but then I get the Cannot Complete Your Request, like it can’t find the Storefronts. But if I revert back to the Basic Authentication it works fine?